
The data is provided by TubeMogul.
Risk, Security, Math, Crypto

Nigel Smart, Professor of Cryptology in the Department of Computer Science at the University of Bristol, will present a paper in Paris this week [Friday 28 May], which makes a step towards a fully practical system to compute on encrypted data. The work could have wide ranging impact on areas as diverse as database access, electronic auctions and electronic voting.
Professor Smart said: “We will present a major improvement on a recent encryption scheme invented by IBM in 2009.”
“Our scheme allows for computations to be performed on encrypted data, so it may eventually allow for the creation of systems in which you can store data remotely in a secure manner and still be able to access it.”
Together with Frederik Vercauteren, from the Katholieke University Leuven in Belgium, Smart has simplifed Gentry’s scheme so that it becomes more practical - not totally so, but an improvement. More information should be available after the paper is published.
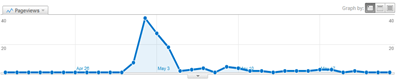
This time last year I made some of my favourite posts. First I celebrated that I had reached about 1,000 visits and 2,000 page views a month, and now I am about double that.
Rethinking Thresholds for Account Lockouts was a simple post asking if the 3-strikes-your-out password policy makes sense. I posted my second Password Roundup #2, and reviewed from Qualys their study on The Half-life of Vulnerabilities is still 30 Days.
I also developed some thoughts why web app bugs don’t get fixed in The $28,000 Question: Project vs. Production Risk, after Jeremiah Grossman estimated that 28,000 well-spent dollars could fix the bugs at many sites.
On the crypto side I broke some news about The cost of SHA-1 collisions reduced to 2^{52}, and took a look at AES-256 and Reputational Risk. The AES post is now on the first page of a Google search for “aes 256” and has brought a steady flow of visits since last May, 1346 in total. I also asked if anyone could verify that the Total Internet computational power = 2^{85} operations, a statement I read in an ECRYPT report. I ended up contacting the authors and nope, no one knows where is came from. Sounds possible though.
I also posted The Sub-Time Crisis in Web 2.0, my thoughts on information overload in Web 2.0. I only used half the text I typed in from my written notes.
A nice how-to article on protecting USB drives with a password and encryption using Windows Vista or 7 and Bitlocker.
Do you carry sensitive data in your pen drive? Then you should carefully keep your pen drive. Oh! You mean you are not that careful too. Then I would suggest that you should password protect your pen drive. Yes folks, you can do this by a simple method. This is an added advantage to Windows Vista and Windows 7 users that they can easily password protect their pen drives with the help of BitLocker Drive Encryption. Its an inbuilt feature of both of these operating systems.
Update: This is a hoax mail leading to a rogue site, so please don't click it. Check out the Lijit blog for details (via Alan).
Just got this from Lijit, the hosting firm for SBN
Perhaps the simplest solution would be to ban marriage outright. Or, better yet, to declare everybody as married to everybody else. But then what would the database engineers do all day?
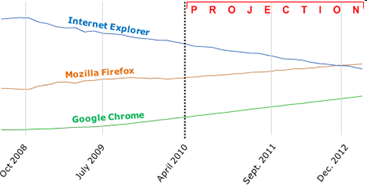
A risk, which isn't immediately obvious, is that this opens up a new world of opportunity for scammers and phishers to register domains that will visually appear very similar to legitimate sites in the address bar, but which will have a base address significantly different, thanks to being registered in a non-Latin script. By relying on alternate character rendering, this could cause problems for users who may not be able to determine the slight differences between otherwise similar looking characters. It also means that software and tools designed to help detect phishing or XSS attacks will have to expand their repertoire significantly to interpret and assess a much broader range of character and rendering sets.
Google stores every piece of data in three centers randomly chosen from the many it operates worldwide in order to guard the company’s ability to recover lost information — but that also makes the data subject to the vagaries of foreign laws and governments, Fischer said. He added that Google was not willing to provide ITS with a list of countries to which the University’s data could be sent, but only a list of about 15 countries to which the data would not be sent.
No personal information that you submit to Facebook will be available to any user of the Web Site who does not belong to at least one of the groups specified by you in your privacy settings.
When you connect with an application or website it will have access to General Information about you. The term General Information includes your and your friends’ names, profile pictures, gender, user IDs, connections, and any content shared using the Everyone privacy setting. ... The default privacy setting for certain types of information you post on Facebook is set to “everyone.” ... Because it takes two to connect, your privacy settings only control who can see the connection on your profile page. If you are uncomfortable with the connection being publicly available, you should consider removing (or not making) the connection
For the last few years I have grown increasing disillusioned with the security industry to the point where after nearly two years of thinking and talking about it I have decided that it’s time for me to move on. There is a long list of frustrations and I have seriously thought about a last detailed shot over the bow with some home truths as I see them. The reality is it will probably not be productive. I had commentary about the security circus and the clowns, ring masters and performance artists that play in the big top; commentary about the lack of genuine computer science that finds its way into security; commentary about the lack of business science that is being adopted (why aren’t security people obsessed by Freakonomics?); commentary about the sad fact that for the most part we are still doing “the same old shit” 15 years after I first started (the definition of insanity is to do the same thing twice and expect a different result); commentary about the farce of PCI (and related standards) and people caring about trivial issues (easy to understand and sensationalist in nature) when looming holes that could have major impacts go unnoticed …….I could go on. People thinking they need “purple dinosaur” features in their security software because some marketing spin says so and commentary about the sheer FUD being pumped out by the marketeers. I have watched an industry spin out of control largely paying lip service to the term risk and watched sectors of it become largely irrelevant outside of their own self-fulfilling set of prophesies. When things go right no one notices (at least outside of security) and when things go wrong everyone points fingers. That’s a tough place to be impactful and remain positive.
The American basically asked "Why are you guys doing so much better than us?". The Japanese businessman is shown extending his fingers and counting off as he says "Your managers are greedy, your workers are lazy, and ...". But before he can finish even just the most obvious reasons, the American interrupts impatiently and says "I know, I know! But what's the trick?"
Excel is your new best friend
We can also stop beating ourselves up on the point that the weakness of IT Risk is the absence of data - the real weakness is poor modelling, and the decisions based on the output of such models.
Mr. Egerstad has stated that there is no security flaw with Tor - the real threat comes from user expectations that their message contents are being protected end-to-end by Tor, when in fact encryption is only applied to internal Tor network communication.
Flaws related to encryption always make good copy, and on occasion, strike at the heart of our fundamental beliefs in security. When encryption falters the whole edifice of security seems shaken.
This may seem an odd question given that since the mid 70's discussions about cryptographic keys have been mainly concerned about their potential shortness.
The Princeton team asked Nature the simple question of whether DRAM is cleared on power loss, and the simple answer is no.
A5/1 has operated unchanged for the last 21 years but it has now reached its cryptographic end-of-life, engulfed by the march of Moore's Law.
Intel's leading chip line, the x86, has steadily progressed from 286, 386, 486, Pentium and so on, but quantum computers will not be "1000-86" devices - unimaginably faster versions of what we have today.
Kapersky has decided to make AV scanning more efficient not by making it faster but by doing less, as determined by risk-based criteria.
It is common that once the torch of enterprise risk management is kindled in the higher corporate echelons, it is passed down the ranks and settles with IT Security people to assume responsibility for the management of IT Risk. And these people are ill-equipped to do so.
Perhaps this reasoning prevailed at Adobe when they recently upgraded their document encryption scheme from AES-128 in v8 to AES-256 in v9. However Adobe later had to announce that v9 in fact offers less security against brute force attacks as compared to v8. What went wrong? They forgot about the spin.
Risk management is about making decisions today that will protect us from the uncertainty of the future. We are not looking for one in a million (the expert) but rather a million and one (the power of many).
We feel more informed, more empowered, and more enamoured with the promise of the omnipotent web. The web 2.0 narrative has worked its magic and we tacitly commit into a seemingly virtuous circle of information inflation.
Navigation and search are just for people who don't have any friends.
Disconnect from Twitter when you are receiving more than one tweet per second.
The AV blacklisting industry has reached a point of diminishing returns - the marginal value of producing additional signatures is minimal, but the underlying model can offer no more advice than to simply keep doing exactly that.
It could be said that PageRank is one part brilliance and two parts daring.
Often business has the “snappy intuitively appealing arguments without obvious problems” - plus Excel … Snappy and plausible usually wins out over lengthy, detailed and correct.
The observation here is that the security function is no longer called upon to critically underwrite the security risks of a project, with the option to reject.
Compound this disconnect between management and technical people over hundreds of thousands of projects at the corporate, national and international levels, spanning the last 3o years, and you have the disaster Ranum is describing (and lamenting).
The worst case scenario for Web 2.0 is that we are heading for a singularity, precipitated by dividing our attention into informational units effectively rated at zero content.
Imagine you posed the following question to a group of top physicists. You asked them to present you with ideas for new research projects where they could assume that the budget included all the money that we have, all the money that has ever been, and the total financial assets of the world for the next 10 million years. Would the resulting proposals be credible?AES-256 puts cryptanalysts on the same research agenda.
So for complex decisions that potentially have the greatest impact in terms of costs and/or reputation, in exactly the circumstances where a thorough risk assessment is required, transparency rather than rigour is the order of the day.
Doctorow remarks that the surprising outcome of this process was the realisation that we are missing a well-known service for handling key escrow in an era of military grade encryption being available to home users.
I don’t really think that there is a cult in operation over Bruce Schneier, but rather a hero was found when security as an industry needed to believe in heroes.
When I look back at crypto now it seems of similar consequence to the proportions of the Sun and Antares - not merely because my professional interests have changed, but in the vast equation that constitutes ERM, crypto is a variable with minor weighting. Its gravitational force is largely exerted on specialists, and rapidly declines (much faster than the inverse square law) beyond that sphere. It's just a pixel on the football-field sized collage of ERM.
So that’s 1,000 years of computation by a cluster that would envelope the earth to a height of one metre.
There are many posts and news articles of late on the TLS Renegotiation Attack. I had hoped that just by skimming a large number of these that some process of web osmosis would magically transfer an understanding of this vulnerability to me.
In the short term (and maybe the longer term as well) Diffie sees the cloud as a matter of trust. He advises to pick your supplier like you pick your accountant.
For each of us the web is a noisy channel, which we express through the need to search, subscribe, aggregate, recommend, post, tweet – in short a great cull of what finds its way onto our screens.
And while the traits of detail, accuracy and correctness are necessary for IT activities, they are fundamentally at odds with the type of messages and opinions that senior managers are expecting.
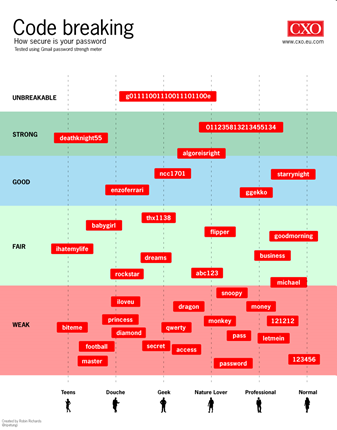
Some articles and posts have focussed on verifying passwords in software as the culprit, which is partly true, but the real issue is not software but insecure programming of software.
Gentry has estimated that building a circuit to perform an encrypted Google search with encrypted keywords would multiply the current computing time by around 1 trillion.
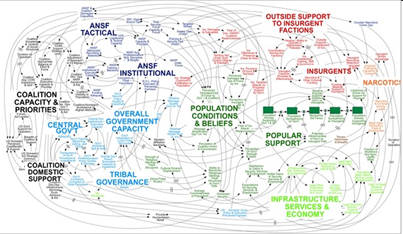
When we started researching this topic we very quickly saw, that the debate whether to pull out the troops, staying or even enforcing is not too much about arguments, it’s a battle of possible scenarios. Every side seems to have their own positive and negative visions of how things will happen in the future if certain steps are done. The resulting map The Afghan Conflict - A Map of Possible Scenarios is the attempt of a summary of the most popular possible scenarios around the afghan conflict, according to a pullout or stay of the Allied troops. And is based on interviews with journalists, politicians and political foundations.
[PowerPoint] slides impart less information than a five-page paper can hold, and that they relieve the briefer of the need to polish writing to convey an analytic, persuasive point. Imagine lawyers presenting arguments before the Supreme Court in slides instead of legal briefs.
In the cloud, the cost of computing will continue to fall bounded only by cost of energy

The NYT has reported on the practice of outsourcing the breaking of captchas to people in Bangladesh, India and China. The work is neither glamorous nor well-paid at 80 cents to $1.20 per 1,000 solved captchas, however there seem to be enough takers nonetheless. The work is farmed out through online exchanges like Freelancer.com, where for example an operator in Bangladesh runs an operation turning out captcha solutions 24 hours a day, seven days a week.
Macduff Hughes, an engineering director at Google says that “Our goal is to make mass account creation less attractive to spammers, and the fact that spammers have to pay people to solve captchas proves that the tool is working.” So we should see captchas as a deterrent rather than a foolproof way of distinguishing people from malware. In fact if people are being employed to break these little authentication puzzles then they are working as intended – to make sure that a person is behind the answer – unfortunately malware is masking a mechanical turk. The inventors of captchas probably did not expect that solving these puzzles could be farmed out so easily using Web 2.0 technology.
The bigger threat probably comes from the direct computer solution to captchas, which can be scaled and provide solutions in real time. I recently posted on the very thorough analysis of the Koobface botnet at abuse.ch, including a section on its captcha breaking network. The captchas are broken in at most 3 minutes, and in many cases just a few seconds. There is also evidence presented by Webroot that audio captchas are also being broken in real time by automated means.
Rodney Joffe, senior vice president and senior technologist at the infrastructure services firm Neustar, gave a keynote presentation on Cloud Computing for Criminals at the recent Cloud Connect conference. Joffe presents some figures which show that the computational size of the Conficker botnet dwarfs the current commercial offerings, based on measuring the number of systems, the number of CPUs and available bandwidth. For Conficker these values are given (estimated?) as
These corresponding measures for Google are 500,000 systems, 1,500,000 CPUs and 1,500 Gbps of bandwidth, with Amazon and Rackspace providing significantly less resources. So Conficker is a massive ad hoc computational structure. But is Conficker really like a cloud service? Joffe says yes because
and further the vendor has good qualifications
This all reminds me of a mail post by Peter Gutmann from 2007 called, World's most powerful supercomputer goes online, referring to the Storm botnet
This doesn't seem to have received much attention, but the world's most powerful supercomputer entered operation recently. Comprising between 1 and 10 million CPUs (depending on whose estimates you believe), the Storm botnet easily outperforms the currently top-ranked system, BlueGene/L, with a mere 128K CPU cores. Using the figures from Valve's online survey
http://www.steampowered.com/status/survey.html
for which the typical machine has a 2.3 - 3.3 GHz single core CPU with about 1GB of RAM, the Storm cluster has the equivalent of 1-10M (approximately) 2.8 GHz P4s with 1-10 petabytes of RAM (BlueGene/L has a paltry 32 terabytes). In fact this composite system has better hardware resources than what's listed at http://www.top500.org.
This may be the first time that a top 10 supercomputer has been controlled not by a government or megacorporation but by criminals. The question remains, now that they have the world's most powerful supercomputer system at their disposal, what are they going to do with it?
And I wonder what the LINPACK rating for Storm is?
And I wonder what the LINPACK rating is for Conficker?